自建 derp 因为避免使用了tailscale公共的derp。所以极大的改善tailscale的网络质量,但如果自建derp 被block或者证书过期等原因不可用时,那整个ts网络就处于不可用的状态。看到ACL的配置drep node 是个数组,说明默认支持多个derp的。因为第一个derp 是在主机上编译安装的,这一次使用docker安装。
docker-compose目录内容
docker/derp# tree -l
.
├── certs
│ ├── acme_account+key
│ └── derp.duomi.website
├── cloudflare.ini
├── docker-compose.yml
└── letsencrypt.ini
cert 目录忽略,是证书脚本自动创建的。
-
cloudflare.ini ,这里使用的cloudflare的长期证书,需要先cloudfalred的DNS-API ,并安装certbot-dns-cloudflare的certbot插件。/docker/derp# cat cloudflare.ini
dns_cloudflare_api_token = your-cloudflare-token(dns-api) -
letsencrypt.ini
docker/derp# cat letsencrypt.ini
dns-cloudflare = True non-interactive = True authenticator = dns-cloudflare dns-cloudflare-credentials = /path/to/docker/derp/cloudflare.ini -
docker-compose.yml
docker/derp# cat docker-compose.ymlversion: "3.7" services: derper: image: ghcr.io/wind4/tailscale-derper:main container_name: derper restart: always environment: - TS_SERVER=https://controlplane.tailscale.com - TS_AUTHKEY=tskey-abcdef1234567890 - TS_EXTRA_ARGS=--hostname=derp-01 - DERP_DOMAIN=derp.yourdomain - DERP_CERT_MODE=letsencrypt - DERP_CERT_DIR=/app/certs - DERP_ADDR=:443 - DERP_STUN=true - DERP_STUN_PORT=3478 - DERP_HTTP_PORT=80 - DERP_VERIFY_CLIENTS=true volumes: - ./letsencrypt.ini:/etc/letsencrypt.ini:ro - ./cloudflare.ini:/cloudflare.ini:ro - ./certs:/app/certs:rw - /var/run/tailscale/tailscaled.sock:/var/run/tailscale/tailscaled.sock:ro ports: - "443:443" - "80:80" - "3478:3478/udp" networks: - derp_network networks: derp_network: driver: bridge -
运行 dockerdocker-compose up -d
配置ACL
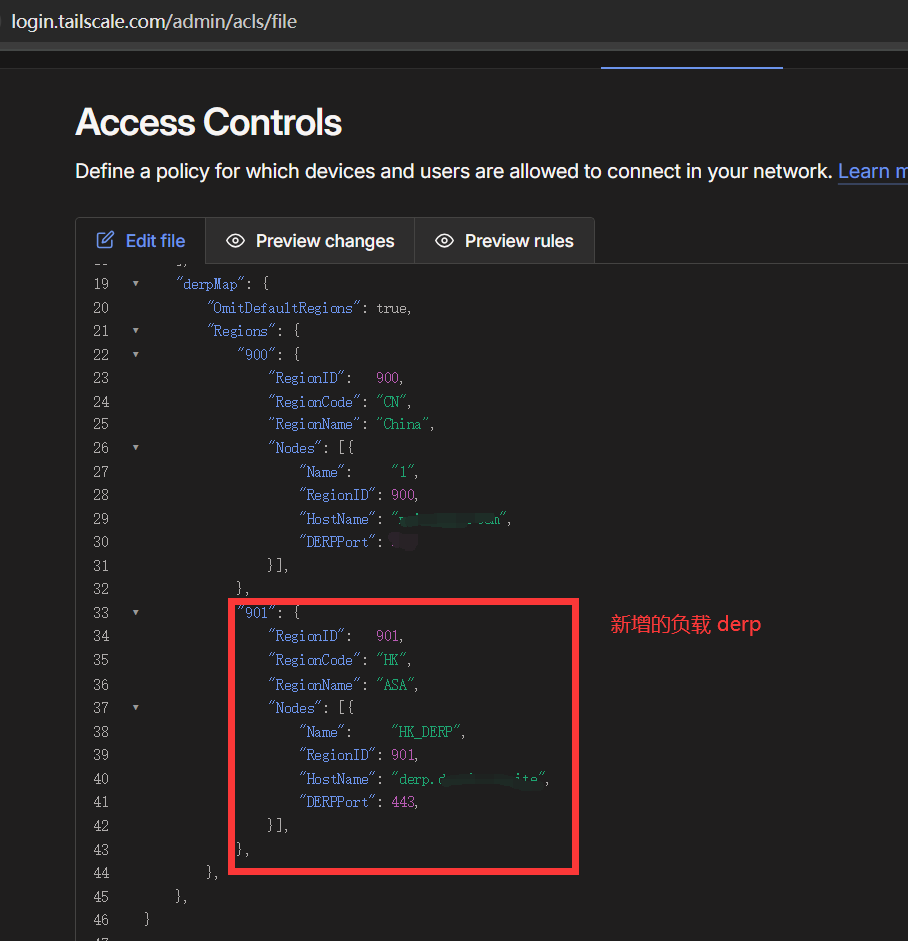
验证derp双持
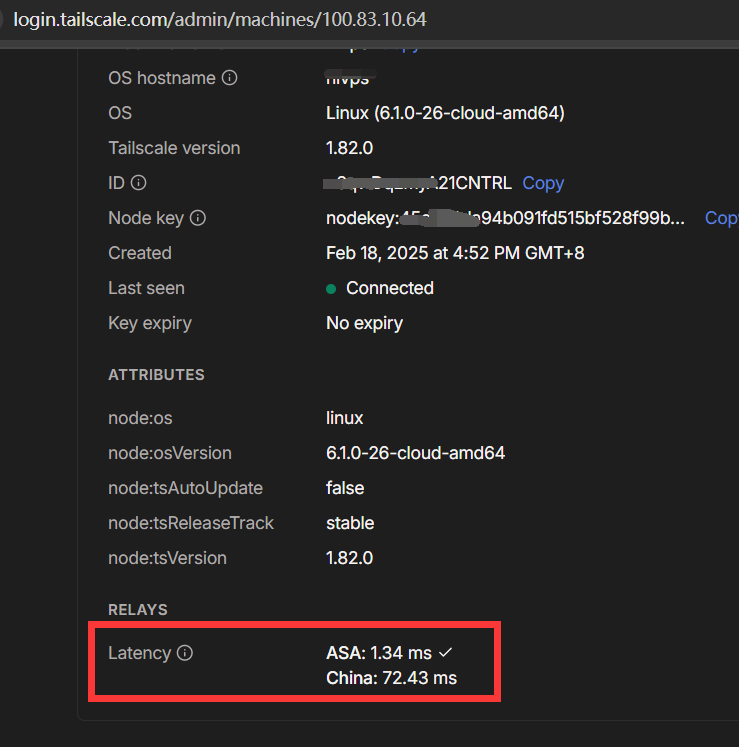
在国内使用显示:Nearest DERP: China
tailscale netcheck
Report:
* UDP: true
* IPv4: yes, 112.32.32.32:3232
* IPv6: no, but OS has support
* MappingVariesByDestIP: false
* PortMapping:
* CaptivePortal: false
* Nearest DERP: China
* DERP latency:
- CN: 21.3ms (China)
- HK: 119.5ms (ASA)